Penetration Testing Basics
What is Penetration Testing?
Before you start diving into any pen testing techniques, I would like to explain what Penetration Testing is and why it's important.
Penetration Testing also referred to as "pen testing", is defined by the National Institute of Standards and Technology (NIST) as "A method of testing where testers target individual binary components or the application as a whole to determine whether intra or inter-component vulnerabilities can be exploited to compromise the application, its data or its environment resources."
Pen testing in any software/hardware environment within any organization is vital, and tests should be conducted periodically. These tests are done to ensure the security of an organization is strong and lacks any holes (also considered vulnerabilities), vulnerabilities, if exploited, can cause severe damage to any system or organization. Tests done on systems act as simulated attacks and allows an organization to make the appropriate changes to their system's security to either alleviate vulnerabilities or just make an organization aware of them to better prepare in the event it's exploited by a possibly malicious actor.
Basic Techniques
Ping
"ping", Is a simple but vital command that is used in several environments. "ping" tests to see if a device or website is reachable from or inside of your network by the requesting device. Although this technique is normally used by system administrators to manually test for connectivity between network devices, this simple command can also be used by malicious actors just to see what machines can be reached.
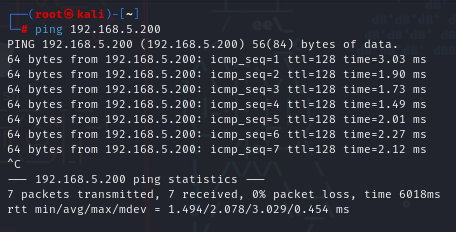
In the image above, I am pinging a Windows XP virtual machine from my Kali Machine
Nmap
"nmap" is another simple yet vital command that is used to collect additional information on devices that you can reach from your device. At its base, "nmap" can tell you which, if any, ports on a target device are open. With this information, an attacker will be able to start seeing which routes they might be able to take in order to gain access to a target device. There are ports with well-known vulnerabilities, and depending on the port and the experience of the attacker, this might give them enough information to gain access to a target device.
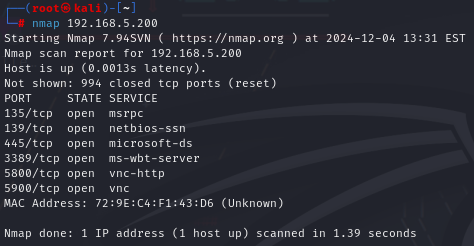
In the image above, I'm targeting the same device, and using nmap shows us which ports are open
(Port 5900 which is used by VNC is an example of a port that if left open and unprotected an attacker with some experience will be able to easily gain access the target device, and with VNC being a remote access service an attacker would be able to easily control that target device)